Multi Factor Authentication
Mydex supports the use of Multi Factor Authentication (MFA) on the Identity as a Service platform (IDaaS), in order to help members strengthen the security of their account and therefore their personal data stored in their PDS.
Supported MFA types
Mydex currently supports the following types of MFA technology:
- Authenticator-style devices (known as Time-based One-Time Passwords, or TOTP). These can be stored on a TOTP-supported application or device (such as Authenticator, Authy, etc) and offer codes that expire every 30 seconds.
- E-mail based one-time codes. These are sent from the Mydex IDaaS platform to the member's nominated e-mail address and expire after 10 minutes if not used.
- SMS based one-time codes. These are sent from the Mydex IDaaS platform to the member's nominated mobile device and expire after 10 minutes if not used.
- Backup / recovery codes. In all three of the above cases (whichever the member elects to use), a set of 10 backup/recovery codes are also generated and displayed to the member. These codes do not automatically expire but can only be used once. The member can regenerate new backup codes by going to their PDS Core Member Account Administration services directly via the People application. They will need their Private Key for their PDS to gain access even if they are logged in with their MydexID already, and if not they will need to Login with their MydexID as well.
- (Coming soon) WebAuthn/FIDO (support for hardware keys/tokens such as Yubikeys and similar products).
In all cases, a valid one-time code can only be used once. The event of submission of both valid and invalid codes gets logged in the member's PDS and Mydex's own intrusion detection systems.
In the case of email and SMS methods, the member's MydexID always appears in the message, to demonstrate that the request is legitimate. Never click on a link that purports to be from Mydex but doesn't mention the MydexID.
How to set up MFA
Multi Factor Authentication can be enabled as part of the registration process, if the application uses Mydex's OpenIDConnect flow for registration.
MFA setup screen during registration
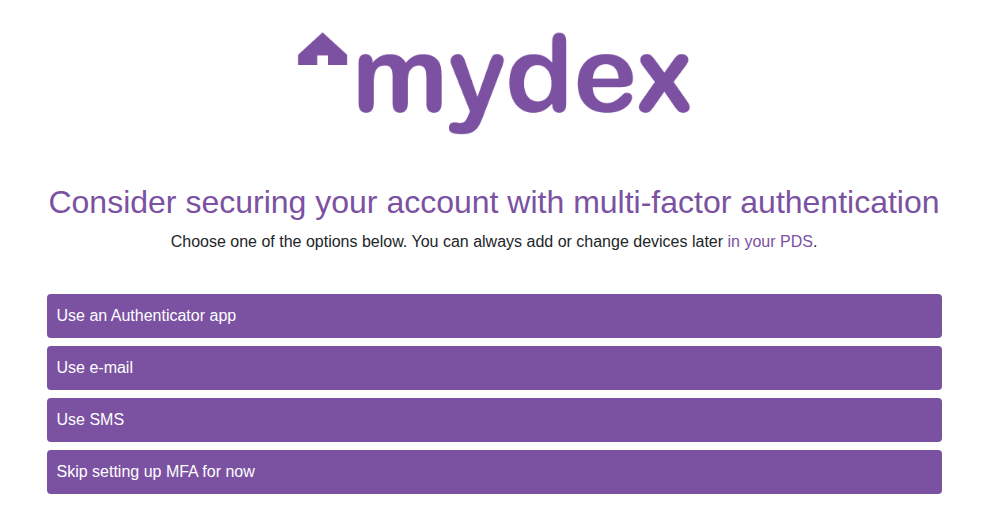
Alternatively, MFA can be set up post-registration via the People application under the My Account -> Settings section of the navigation.
How to manage MFA
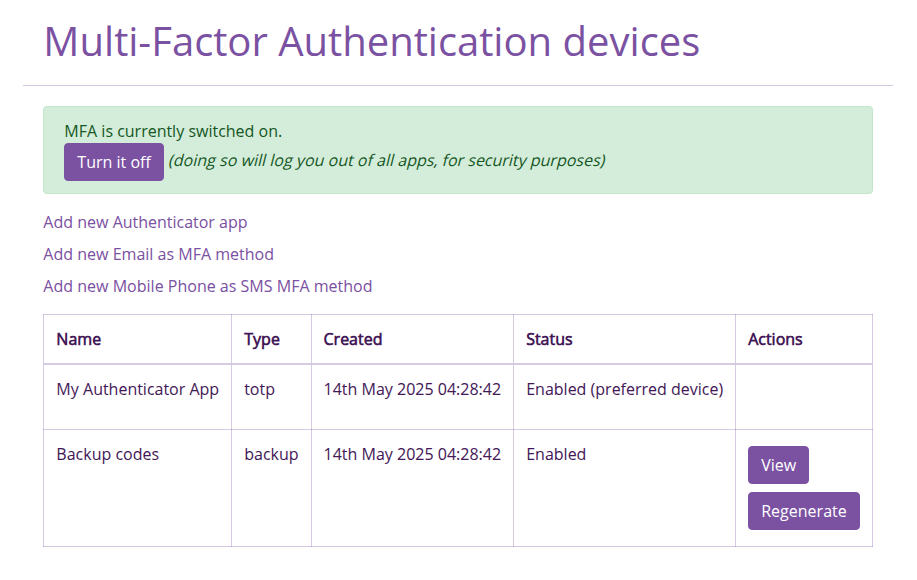
The Member can manage their MFA settings via the People application under the My Account -> Settings section of the navigation. In this area, the member can perform the following actions:
- Enable or disable MFA entirely
- Add, enable, disable or delete different types of MFA device
- Set a specific MFA device as the preferred device
- View and regenerate backup/recovery codes
The preferred device cannot be disabled or deleted. Instead, a separate MFA device must be added and set as preferred before the original device can be disabled or deleted.
In addition to the backup codes, if a member has multiple, enabled MFA devices, they will be able to request the use of one of those non-preferred devices at login time, should their preferred device be unavailable at that time.
The MFA secrets associated with each device are stored within the member's own PDS.
MFA management screen in the MEL
Auditing the use of MFA
Members can inspect their Identity Services Log in their PDS, which (in addition to login and logout events) will show the following types of event:
- MFA device being added, removed, enabled, disabled, or set as preferred
- Valid or invalid codes being used
- Backup codes being regenerated
These events will also log the IP address that made the request.
How Subscribers can mandate the requirement for MFA
If a Subscriber is developing an application that:
- Is participating in the Mydex OpenID Connect (OIDC) system for sign-on with MydexID as a Relying Party (RP), and
- mandates that the member use MFA in order to make use of their service,
Mydex can accommodate this by adding the mfa:mandated scope to the RP's OIDC Client. The RP must send this scope as part of commencing OIDC journeys to make use of the service.
When this scope is present for a valid OIDC Client, Mydex's Login and Consent Application (LaCa) will enforce that the member must set up (or have already set up) MFA as part of either Registration or Login flows. If the member has not set up MFA, there is no 'Skip MFA for now' option in the MFA setup screen following registration or login, and they will not be able to complete authentication.
(Coming soon) Selective MFA (e.g for specific journeys)
Mydex is exploring new innovative ways to make use of MFA in ways that strike the right balance between security and convenience for the member. These include:
- Requiring MFA for specific journeys or actions that contextually require an additional security check (even if the member was already logged in). We call this 'graduated' MFA.
- Skipping MFA for journeys that present a low-level of risk and which might otherwise add friction for the member to complete a task.
- Allowing a member to skip MFA for specific applications that they sign into with their MydexID but not others