Using Mozilla Persona
Introduction
Mozilla Persona is a cross-browser login system, where a user logs in to a website using an email address as an identity which is authenticated by the provider of the email address acting as an Identity Provider, in this case Mydex CIC. There are a number of benefits that arise from using the Persona service:
- Persona completely eliminates site-specific passwords, freeing users and websites from the burden of creating, managing, and securely storing passwords.
- Persona is easy to use. With just two clicks a Persona user can sign into a new site like 123done.org, bypassing the friction associated with account creation.
- Persona is easy to implement. Organistations can add Persona to a site within a single afternoon.
- There's no lock-in. Subscribing organisations get a verified email address for all of their users, and users can use any email address with Persona.
When you register with the Mydex CIC service, you are automatically provided with an email address from the MydexID domain (eg alice@mydexid.org). This address can then be used to log into websites that support the Mozilla Persona login service. The benefit for Mydex members is that their core MydexID can be used wherever SAML, OpenIDconnect or Persona is supported. It is one ID for life.
How browsers interact with Mydex as an IdPS
To demonstrate how Browsers and Mydex acting as an IdP interact, let's look at what needs to happens the first time alice@mydexid.org tries to use Persona to log into a website.
- Alice's browser fetches the support document from https://idp.mydexid.org/.well-known/browserid.
- Alice's browser invisibly loads the provisioning page for mydexid.org and asks it to sign a public key certifying Alice's identity.
- Before signing the key, mydexid.org needs proof that the user really is Alice, so it tells the browser that she needs to authenticate.
- Alice's browser shows Alice the authentication page for mydexid.org and she signs in, establishing a new session at mydexid.org.
- Alice's browser reloads the provisioning page and again asks it to sign a public key certifying Alice's identity.
- The provisioning page can verify Alice's identity by inspecting the new session. Satisfied, it signs a certificate containing Alice's public key, her email address, and an expiration date for the certificate.
For the duration of the signed certificate, Alice's browser can create valid identity assertions for alice@mydexid.org whenever she wants to log into a web site which supports Persona. Steps 3-5 can be skipped if Alice already has a valid session with mydexid.org, for example, from logging into a community site or an intranet portal.
The process can be demonstrated by logging into 123done.org
-
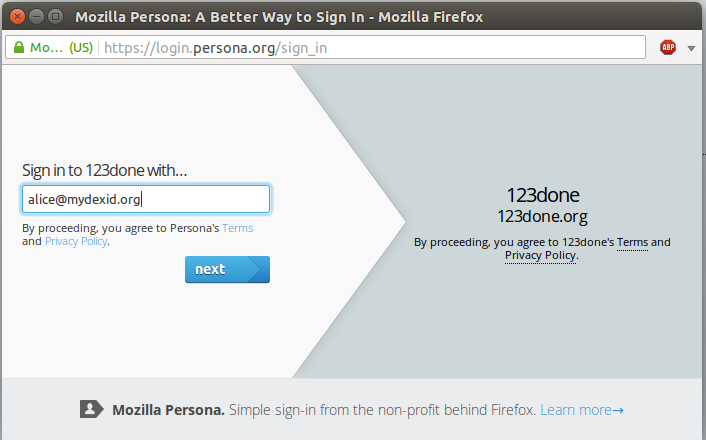
Click sign in on the homepage.

-
Enter your MydexID full email address (eg alice@mydexid.org).
-
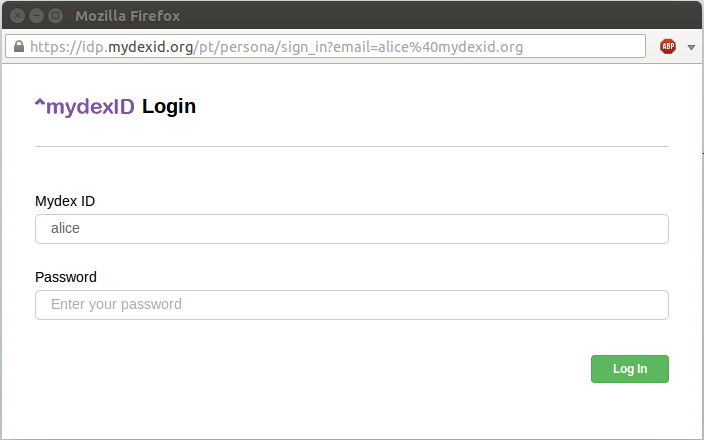
The individual is then taken to the authentication page. Enter your MydexID and password.
-
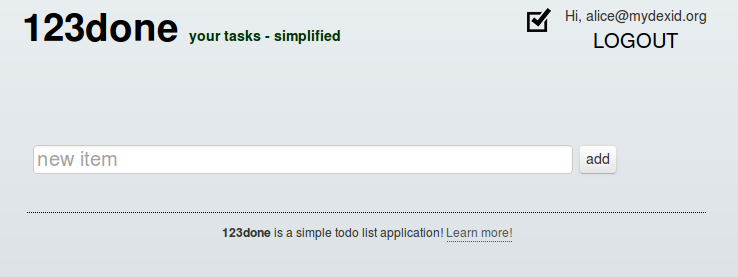
The individual is then certified and logged in and can begin to use the website.
Mozilla Persona only supports authentication
Mozilla Persona only supports authentication. It does not support a registration process for new visitors to your website. If you require registration services we would recommend using SAML based protocol as this will allow Mydex Identity Services to manage the initial registration, subsequent authentication and any password management activities for you. The entire process can be controlled from within your own website using our API’s. The read more about using SAML for a full IdP service please click here.
Implementing Mozilla Persona support on your website
There is no work required from Mydex CIC to support your use of Mozilla Persona.
The standard implementation guides are published directly by the Mozilla Persona Project website. The key steps are summarised below:
- Include the Persona JavaScript library on your pages.
- Add "login" and "logout" buttons.
- Watch for login and logout actions.
- Verify the user's credentials.
- Review best practises.
A more detailed explanation of these steps can be found on the Mozilla Website here.